

Endpoint Detection and Response (EDR) is cybersecurity protection software that detects threats on end-user devices (endpoints) in an organization. Across a large, clamorous, worldwide arena of cybersecurity solutions, EDR stands out as a distinct category of telemetry tools that provide continuous monitoring of endpoints to identify and manage adversarial cyber threats such as malware and ransomware.
EDR technology is also sometimes referred to as endpoint detection and threat response (EDTR).
As a cyber telemetry tool, EDR solutions collect data from endpoints as part of threat monitoring and can correlate data from across an entire infrastructure, including its endpoint tools and applications. So EDR tools can be very powerful as threat protection and attack context technologies and formidable endpoint security measures.


EDR analyzes and monitors all ongoing activities for devices connected to your network and provides real-time threat detection and visibility for automated threat response for security teams for threat hunting.
EDR Tools were first named in 2013 by Gartnerand defined specifically as endpoint protection deployed to:
EDR technology is a class of endpoint monitoring software that is uniquely trained to detect suspicious and/or anomalous activity on endpoints. Early on, this type of detection immediately separated EDR from antivirus (AV) tools and EPP (Endpoint Protection Platforms) – AV/EPP tend primarily to identify and act on specific signatures and hashes of malware (known-good and known-bad signature instances).
AV and EPP solutions block or quarantine known-bad objects and files. But EDR monitors and correlates anomalies and suspicious activity on endpoints, then raises a detection alert with context and severity details that the security teams, cyber threat intelligence teams, and threat hunting teams can use for investigation and remediation/response.
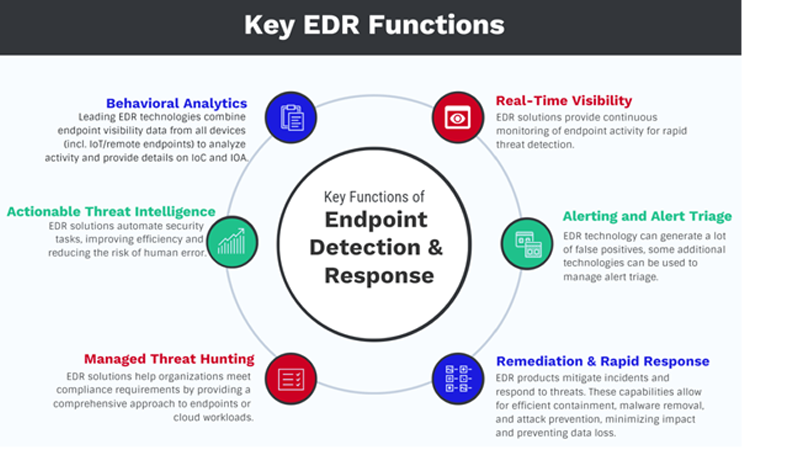
Selecting the right Endpoint Detection and Response (EDR) vendor is critical for organizations looking to bolster their cybersecurity posture. We at MaximAlert can help you with the vital factors to consider to ensure you choose the best EDR security vendor for your needs:
The heart of an EDR system lies in its ability to detect and respond to threats effectively. Assess the vendor's capabilities in identifying a wide range of threats, from malware and ransomware to sophisticated, state-sponsored attacks. Look for advanced features like behavioral analysis, anomaly detection, and AI-driven insights. The system should offer real-time response capabilities, allowing you to quickly isolate infected devices, block malicious activity, and remediate threats.
Your EDR solution should seamlessly integrate with your existing security and IT infrastructure. This includes compatibility with other security solutions (firewalls, antivirus, and SIEM systems) and IT management tools. Proper integration enhances visibility across your network and streamlines response efforts. Check if the vendor supports standard integration protocols and provides APIs for custom integrations.
Consider how well the EDR solution can scale with your organization. It should handle an increasing number of endpoints without significant performance degradation. Evaluate the impact of the EDR software on endpoint performance, ensuring it does not interrupt day-to-day operations or reduce system efficiency.
The usability of the EDR platform is crucial for effective threat hunting and incident response. Look for a user-friendly interface that provides clear, actionable insights. The platform should offer comprehensive reporting and visualization tools for threat analysis and decision-making. Additionally, assess the system's management features, such as policy configuration, alert customization, and automated response actions.

Strong vendor support and comprehensive training are essential to successfully deploying and operating an EDR solution. Investigate the vendor's support structure, including availability, response times, and types of support offered (phone, email, online chat). Inquire about training resources and programs to ensure your team can use and maintain the EDR system effectively.
Research the vendor's reputation within the cybersecurity industry. Look for independent reviews, customer testimonials, and case studies. Consider the vendor's history, including how long they have been in business, financial stability, and track record for innovation and customer satisfaction.
Ensure the EDR solution complies with relevant regulations and industry standards, such as GDPR, HIPAA, or PCI DSS. The vendor should provide features that support compliance efforts, including data encryption, access controls, and comprehensive logging and reporting capabilities.
Evaluate the total cost of ownership of the EDR solution, including initial purchase costs, implementation fees, and ongoing maintenance expenses. Consider the potential return on investment, factoring in the costs associated with data breaches and cybersecurity incidents. A higher-priced solution may offer more excellent value if it significantly reduces the risk of costly security breaches.
By carefully considering these factors, MaximAlert can help organizations choose an EDR vendor that meets their security needs and aligns with their business objectives, budget, and operational capabilities. The right EDR solution will enhance your cybersecurity defenses, enable rapid response to incidents, and provide valuable insights into threat activities on your endpoints.